Cybersecurity for Medical Devices
Cybersecurity is a major new issue for manufacturers of Medical Devices (MD) that embed (or are) software, it also concerns organizations that store and handle sensitive data (typically: personal health data).
Technology creates new risks of attack, which must be managed through a cybersecurity process.
The task is complex, but the good news is that medical device manufacturers already have all the tools (processes) to tackle this challenge.
This article gives the state of the art in medical device cybersecurity, to provide an overall view of a cybersecurity management process.
A review of vigilance issues associated with cybersecurity is proposed at the end of the article.
What Medical Devices are concerned by Cybersecurity?
Security issues are applicable to any medical device software and particularly to any connected medical device.
Therefore, cybersecurity should not be limited to Internet-connected MDs: a simple USB port or a simple programming interface can be entry points for attacks!
Regulatory and normative context in medical devices cybersecurity
Regulation (EU) 2017/745
The requirements are of course to be found in Regulation (EU) 2017/745, Annex I proposes general requirements applicable to software, Annex II details the expectations of the technical file. Some requirements echo cybersecurity:
developed and manufactured in accordance with the state of the art taking into account the principles of development life cycle, risk management, including information security (…) set out minimum requirements concerning hardware, IT networks characteristics and IT security measures, including protection against unauthorised access (…) testing performed both in-house and in a simulated or actual user environment (…) different hardware configurations and, where applicable, operating systems identified in the information supplied (…)
Guidelines for the cybersecurity of medical devices
While an MDCG guide for cybersecurity is feverishly awaited, we currently have many guides (and requirements) available, written by relevant authorities very concerned about the subject:
- IMDRF: IMDRF Guide for Cybersecurity
- ANSM: Guide on the cybersecurity of medical devices
- Health Canada: Guidance Document for Medical Device Cybersecurity
- TGA: Guidance on “Medical device cybersecurity guidance for industry”
- FDA: Guidance on “Cybersecurity”
You can also consult the work of scholarly societies: ENISA, ANSII (and its EBIOS method) and NIST in particular.
Standards for the cybersecurity of medical devices
- The AAMI TIR57 standard is certainly the most comprehensive
- The UL 2900-1 and UL 2900-2-1 standards (MD connected to a network) offer testing, a UL certificate can be obtained via an approved laboratory
- ISO/TC 215 committee standards (including the IEC 80001-x-x series)
Cybersecurity: a matter of risk management
Before defining a cybersecurity management process, you need to understand that these activities are in fact risk management activities, the vocabulary used in cybersecurity should convince you of this:
Cybersecurity is about managing computer threats (risks).
Threats are associated with computer vulnerabilities (hazards).
A threat materializes in a computer attack (the dangerous situation), which may result in harm (patient or even just data in case of regulatory consequences).
It will therefore be a question of managing cybersecurity risks: identifying them, controlling them and monitoring them.
The objectives of cybersecurity
In addition to the general objectives of performance and security, it will be necessary – when handling data/information – to take into account the 4 main objectives of information systems security :
- Guarantee confidentiality
- Guarantee the integrity of data
- Guarantee the accessibility
- Guarantee the auditability of the system
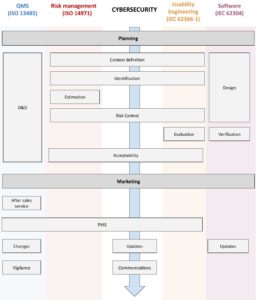
Cybersecurity management process
It is highly recommended that you manage a dedicated cybersecurity procedure, otherwise integrate the requirements into your risk management or software lifecycle procedure.
Your system is already substantial, cybersecurity will use many of your existing processes :
- Risk Management (ISO 14971) and Usability Engineering (IEC 62366-1)
- Lifecycle of software (IEC 62304)
- Software validation (IEC 82304-1 for standalone software and IEC 60601-1 for embedded software)
- Quality Management System (ISO 13485)
- Post-Market Surveillance (ISO TR 20416)
- And supporting processes, such as “Service and delivery”, “Document management”, “Stakeholder communications”…
The Flowchart below highlights the cybersecurity activities, most often shared with other processes:
The stages in the cybersecurity management process are as follows:
- Planning
- Contextualization
- Identification of risks
- Risk assessment: according to ISO 14971 and, if needed, according to cybersecurity-specific methods, such as the Computer Vulnerability Score: CVSS
- Control of risks
- Design and development
- Verification, laboratory testing is possible
- Validation, including Usability Engineering testing
- Management of information provided
- Post-market surveillance and watch
- Corrective and preventive actions (including updates, patching, communication about cybersecurity issues…) the computer vulnerability score: CVSS
These activities will be implemented according to a risk-based approach: an initial Risk Analysis will quantify the cybersecurity risks, your work will be legitimately proportionate to these risks.
Analysis of actual cybersecurity-related vigilance events
An analysis of vigilance events leads to considerably weighted cybersecurity issues in the medical device sector: alerts are rare and exclusively preventive.
Vigilance events most often involve large companies, with AIMD (Active Implantable Medical Device) being particularly targeted.
Problems target opportunities for unauthorized access, malicious reprogramming and authentication bypass. The causes are frequently attributable to the means of communication or reprogramming and the operating system.
It is interesting to go further, the site cyberveille-sante.gouv.fr (French) has a section dedicated to the watch for health alerts, with events most often without consequences:
- 28% of alerts concern medical devices, 72% concern Health Institutions
- MDs are victims of “vulnerabilities”
- Only 7% of events are attacks by hackers
- 2% fishing, 12% ransomware
- 17% of alerts involve compromised databases
- 16% of alerts were as a result of data leaks
- The causes, apart from technical problems, are varied: human error (4%), email hacking (4%) even hardware theft (3%)